精彩评论
- 张麻子是杂种(5天前)
从有人以来就没有比张麻子更邪恶 张口闭口为人民,害死几千万人还为人民,为自己的皇位还差不多,...
评:深度解析《让子弹飞》 al2359(3年前 (2023-02-06))
求科学离线插件,谢谢!34401355@qq.com
评:改版梅林固件安装SS【shadowsocks】科学上网插件教程al2359(3年前 (2023-02-06))
求科学离线插件,谢谢!!!
评:改版梅林固件安装SS【shadowsocks】科学上网插件教程
服务器系统版本:
CentOS / 7.3 x86_64 (64bit)
准备工作:
搭建PPTP服务和搭建L2TP/IPSec服务均需要设置内核支持转发
编辑sysctl.conf
|
vim /etc/sysctl.conf
|
在末尾添加:
|
1
|
net.ipv4.ip_forward = 1
|
保存并退出,执行以下命令使其生效
|
1
|
sysctl -p
|
|
1
|
cat /dev/ppp |
结果显示:
cat: /dev/ppp: No such file or directory 或者 cat: /dev/ppp: No such device or address
可以继续
|
1
|
yum install -y ppp iptables pptpd |
安装之前,可以更新yum源
1、编辑pptpd.conf
|
1
|
vim /etc/pptpd.conf |
添加或去掉“#”以下字段并保存退出:
|
1
2
|
localip 172.100.127.1 本机内网ipremoteip 172.100.127.100-120,172.100.127.245 VPN分配网段 |
2、编辑options.pptpd
|
1
|
vim /etc/ppp/options.pptpd |
找到ms-dns,去掉#号注释修改为
|
1
2
|
ms-dns 114.114.114.114ms-dns 8.8.4.4 |
保存并退出
3、编辑chap-secrets设置VPN用户名密码
|
1
|
vim /etc/ppp/chap-secrets |
添加一行(注意:用户名密码区分大小写)
|
1
2
|
# client server(/etc/ppp/options.pptpd 中对应的name pptpd) secret IP addresses root pptpd 123456 * |
1、启动防火墙
|
1
|
systemctl start firewalld |
2、启用NAT转发(必须启用此功能)
|
1
|
firewall-cmd --permanent --add-masquerade |
3、开启47及1723端口
|
1
2
|
firewall-cmd --permanent --zone=public --add-port=47/tcpfirewall-cmd --permanent --zone=public --add-port=1723/tcp |
4、设置规则
|
1
2
3
4
5
|
firewall-cmd --permanent --direct --add-rule ipv4 filter INPUT 0 -p gre -j ACCEPTfirewall-cmd --permanent --direct --add-rule ipv4 filter OUTPUT 0 -p gre -j ACCEPTfirewall-cmd --permanent --direct --add-rule ipv4 FORWARD 0 -i ppp+ -o eth0 -j ACCEPTfirewall-cmd --permanent --direct --add-rule ipv4 FORWARD 0 -i eth0 -o ppp+ -j ACCEPTfirewall-cmd --permanent --direct --passthrough ipv4 -t nat -I POSTROUTING -o eth0 -j MASQUERADE -s 172.100.127.0/24 (内网网段) |
5、重启防火墙
|
1
|
firewall-cmd --reload |
1,安装firewall-config,需重新打开命令行终端
|
1
|
yum -y install firewall-config |
2, 打开firewall-config,xshell 需要使用xmanager
|
1
|
firewall-config |
3,切换到permanent模式
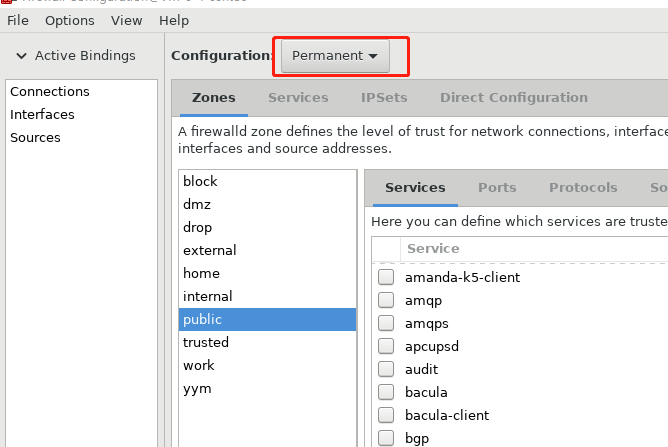
4,打开public zone的gre服务:
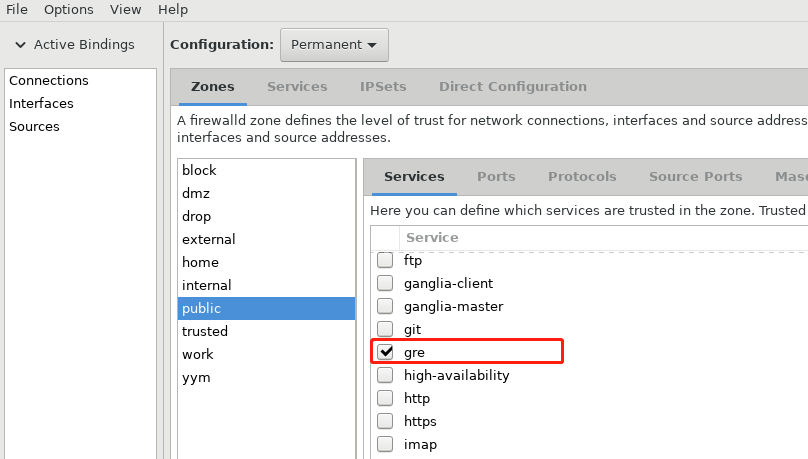
5,添加端口1723和47
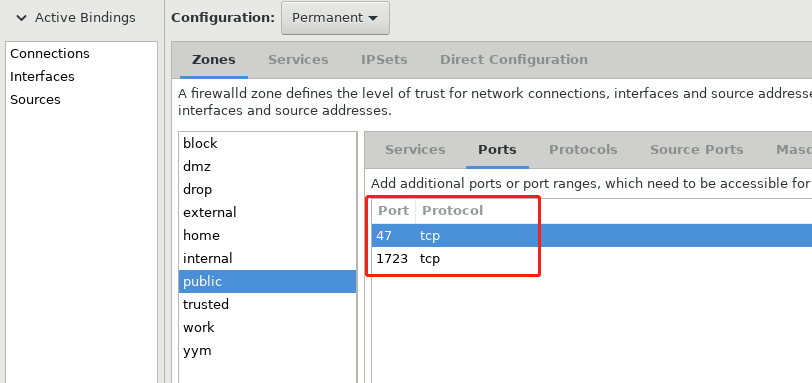
6,打开net转发:
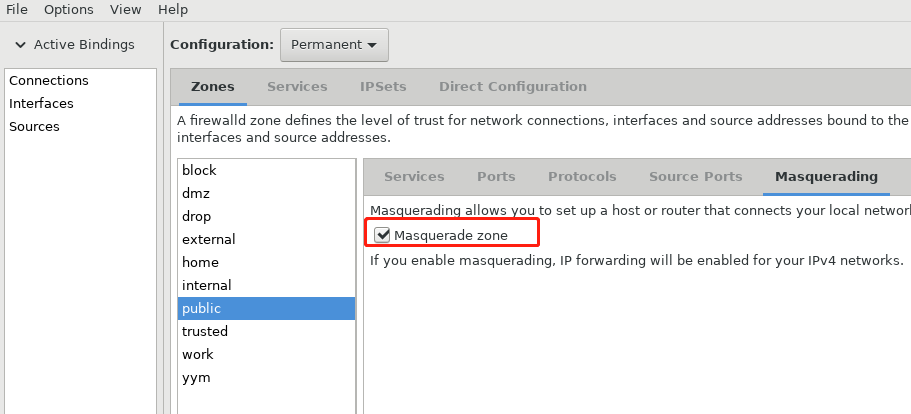
7,添加富规则,配置转发:
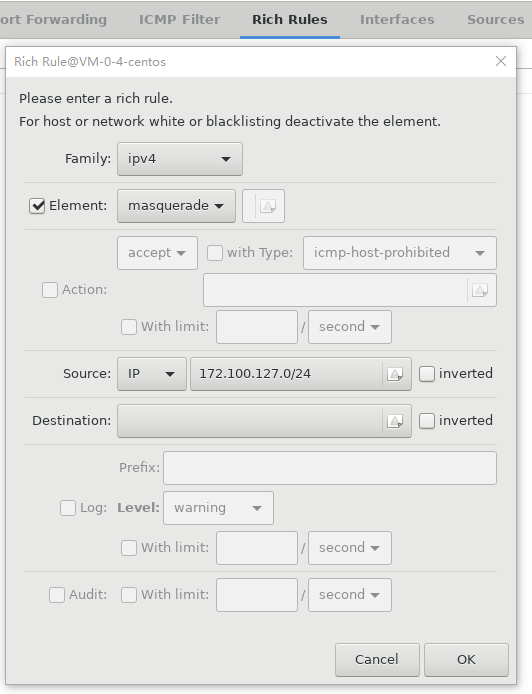
|
1
|
systemctl start pptpd<br><br>查看服务状态systemctl status pptpd |
设置pptpd服务开机自启
|
1
|
systemctl enable pptpd |
至此,PPTP服务已搭建完成,可以使用Windows或Mac通过VPN连接。
|
1
|
yum install -y epel-release |
|
1
|
yum install -y xl2tpd libreswan lsof |
1、编辑xl2tpd.conf
|
1
|
vim /etc/xl2tpd/xl2tpd.conf |
修改以下内容
|
1
2
3
4
5
6
7
8
9
10
|
[lns default]ip range = 172.100.112.100-172.100.112.125 VPN 分配的网段local ip = 172.100.112.1 本机内网IPrequire chap = yesrefuse pap = yesrequire authentication = yesname = LinuxVPNserverppp debug = yespppoptfile = /etc/ppp/options.xl2tpdlength bit = yes |
2、编辑options.xl2tpd
|
1
|
vim /etc/ppp/options.xl2tpd |
修改以下内容
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
ipcp-accept-localipcp-accept-remotems-dns 114.114.114.114ms-dns 8.8.8.8# ms-dns 192.168.1.1# ms-dns 192.168.1.3# ms-wins 192.168.1.2# ms-wins 192.168.1.4noccpauth#obsolete: crtsctsidle 1800mtu 1410mru 1410nodefaultroutedebug#obsolete: lockproxyarpconnect-delay 5000 |
3、编辑l2tp-ipsec.conf(没有则新建)
|
1
|
vim /etc/ipsec.d/l2tp-ipsec.conf |
添加或修改以下内容
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
config setup nat_traversal=yes virtual_private=%v4:10.0.0.0/8,$v4:192.168.0.0/16,%v4:172.16.0.0/12 oe=off protostack=netkeyconn L2TP-PSK-NAT rightsubnet=vhost:%priv also=L2TP-PSK-noNATconn L2TP-PSK-noNAT authby=secret pfs=no auto=add keyingtries=3 rekey=no ikelifetime=8h keylife=1h type=172.100.112.1 leftprotoport=17/1701 right=%any rightprotoport=17/%any |
4、编辑chap-secrets设置VPN用户名密码
这个配置文件和PPTPD的用户名密码配件文件共用,参考PPTP的设置
1、允许ipsec服务
|
1
|
firewall-cmd --permanent --add-service=ipsec |
2、允许1701、4500端口
|
1
2
|
firewall-cmd --permanent --add-port=1701/updfirewall-cmd --permanent --add-port=4500/upd |
3、启用NAT转发
搭建PPTP时,如果已开启可忽略
|
1
|
firewall-cmd --permanent --add-masquerade |
4、重启防火墙
|
1
|
firewall-cmd --reload |
|
1
|
vim /etc/sysctl.conf |
添加以下内容
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
net.ipv4.conf.all.accept_redirects = 0net.ipv4.conf.all.rp_filter = 0net.ipv4.conf.all.send_redirects = 0net.ipv4.conf.default.accept_redirects = 0net.ipv4.conf.default.rp_filter = 0net.ipv4.conf.default.send_redirects = 0net.ipv4.conf.eth0.accept_redirects = 0net.ipv4.conf.eth0.rp_filter = 0net.ipv4.conf.eth0.send_redirects = 0net.ipv4.conf.eth1.accept_redirects = 0net.ipv4.conf.eth1.rp_filter = 0net.ipv4.conf.eth1.send_redirects = 0net.ipv4.conf.eth2.accept_redirects = 0net.ipv4.conf.eth2.rp_filter = 0net.ipv4.conf.eth2.send_redirects = 0net.ipv4.conf.ip_vti0.accept_redirects = 0net.ipv4.conf.ip_vti0.rp_filter = 0net.ipv4.conf.ip_vti0.send_redirects = 0net.ipv4.conf.lo.accept_redirects = 0net.ipv4.conf.lo.rp_filter = 0net.ipv4.conf.lo.send_redirects = 0net.ipv4.conf.ppp0.accept_redirects = 0net.ipv4.conf.ppp0.rp_filter = 0net.ipv4.conf.ppp0.send_redirects = 0 |
使其修改生效
|
1
|
sysctl -p |
1、启动ipsec服务
|
1
|
systemctl start ipsec |
2、检查ipsec配置
|
1
|
ipsec verify |
3、设置ipsec开机自启
|
1
|
systemctl enable ipsec |
4、启动xl2tp服务
|
1
|
systemctl start xl2tp |
5、设置xl2tp开机自启
|
1
|
systemctl enable xl2tpd |
至此,L2TP/IPSec服务已搭建完成,可以使用Windows或Mac通过VPN连接。
「梦想一旦被付诸行动,就会变得神圣,如果觉得我的文章对您有用,请帮助本站成长」
上一篇:芬蘭政府確定要加入北約
从有人以来就没有比张麻子更邪恶 张口闭口为人民,害死几千万人还为人民,为自己的皇位还差不多,...
评:深度解析《让子弹飞》求科学离线插件,谢谢!34401355@qq.com
评:改版梅林固件安装SS【shadowsocks】科学上网插件教程求科学离线插件,谢谢!!!
评:改版梅林固件安装SS【shadowsocks】科学上网插件教程